了解更多:端口扫描工具终极用法 | 至察助安 – 网络安全干货博客
为什么要做c段探测,运营商分配给IDC机房地址时大部分都是连续IP地址,租给客户(渗透目标)时很大概率会分配同C段内IP地址(除非目标就一个IP地址),使用工具扫描可以探测出同段服务。
扫描工具UP主经常用的有三个:
- Nmap
- Masscan
- zmap
Nmap用法
Nmap(Network Mapper,网络映射器) 是一款开放源代码的网络探测和安全审核的工具。老规矩先放出我最常用的命令组合方式,想了解原理继续看,不想了解直接套用就可以。
sudo nmap -v -sS -p8000-9000 -Pn -T4 -A 124.*.8.254 --script http-methods --script-args http.useragent="Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0" |
-v 实时输出扫描详情
vulab@sechelper:~/masscan$ nmap -v 124.*.8.254 Starting Nmap 7.80 ( https://nmap.org ) at 2022-09-05 04:01 UTC Initiating Ping Scan at 04:01 Scanning 124.*.8.254 [2 ports] Completed Ping Scan at 04:01, 0.03s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 04:01 Completed Parallel DNS resolution of 1 host. at 04:01, 0.01s elapsed Initiating Connect Scan at 04:01 Scanning 124.*.8.254 [1000 ports] Discovered open port 443/tcp on 124.*.8.254 Discovered open port 22/tcp on 124.*.8.254 Discovered open port 80/tcp on 124.*.8.254 ... |
-A 全面扫描
vulab@sechelper:~$ nmap -A 124.*.8.254 # nmap -A 124.*.8.1/24 扫描C段存活端口 Starting Nmap 7.80 ( https://nmap.org ) at 2022-09-04 12:09 UTC Nmap scan report for 124.*.8.254 Host is up (0.037s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 22/tcp open tcpwrapped |_ssh-hostkey: ERROR: Script execution failed (use -d to debug) 80/tcp open tcpwrapped |_http-server-header: nginx/1.18.0 (Ubuntu) 443/tcp open tcpwrapped |_http-server-header: nginx/1.18.0 (Ubuntu) | ssl-cert: Subject: commonName=navi.sechelper.com | Subject Alternative Name: DNS:navi.sechelper.com | Not valid before: 2022-08-27T00:00:00 |_Not valid after: 2023-08-27T23:59:59 | tls-alpn: |_ http/1.1 | tls-nextprotoneg: |_ http/1.1 |
-Pn 禁ping扫描,扫描前不ping(不加这个参数Nmap会ping目标地址)
vulab@sechelper:~$ nmap -Pn 124.*.8.254 Starting Nmap 7.80 ( https://nmap.org ) at 2022-09-04 13:02 UTC Nmap scan report for 124.*.8.254 Host is up (0.035s latency). Not shown: 997 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 443/tcp open httpsNmap done: 1 IP address (1 host up) scanned in 25.80 seconds |
-p 指定端口
vulab@sechelper:~$ nmap -p22,21,8000-9000 124.*.8.254 Starting Nmap 7.80 ( https://nmap.org ) at 2022-09-04 21:20 CST Nmap scan report for 124.*.8.254 Host is up (0.0031s latency).PORT STATE SERVICE 22/tcp open sshNmap done: 1 IP address (1 host up) scanned in 0.34 seconds |
-sP 使用ping探测主机存活,不扫描端口
vulab@sechelper:~$ nmap -sP 192.168.111.1/24 Starting Nmap 7.80 ( https://nmap.org ) at 2022-09-04 12:31 UTC Nmap scan report for _gateway (192.168.111.2) Host is up (0.00032s latency). Nmap scan report for sechelper (192.168.111.133) Host is up (0.000091s latency). |
-sS syn扫描/半开放扫描,准确率太低
vulab@sechelper:~$ sudo nmap -sS 124.*.8.254 ... Not shown: 979 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 443/tcp open https 8002/tcp closed teradataordbms 8042/tcp closed fs-agent 8088/tcp closed radan-http 8090/tcp closed opsmessaging ...Nmap done: 1 IP address (1 host up) scanned in 867.60 seconds |
-sT 连接扫描,准确率高
vulab@sechelper:~$ nmap -sT 124.*.8.254 Starting Nmap 7.80 ( https://nmap.org ) at 2022-09-04 14:14 UTC Nmap scan report for 124.*.8.254 Host is up (0.037s latency). Not shown: 997 filtered ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http 443/tcp open httpsNmap done: 1 IP address (1 host up) scanned in 14.17 seconds |
| 状态 | 含义 |
|---|---|
| open | 端口开着,正在被使用 |
| closed | 端口已关闭 |
| filtered | 扫描被阻拦, 无法确定端口是否开放 |
| unfiltered | 端口可被访问,但不能确定是开放还是关闭 |
表一 Nmap 端口状态表
-T 提升扫描速度,0-5,数值越高速度越快
vulab@sechelper:~/masscan$ nmap -A -v -p80 -T4 124.*.8.254 ... PORT STATE SERVICE VERSION 80/tcp open http nginx 1.18.0 (Ubuntu) | http-methods: |_ Supported Methods: GET HEAD POST |_http-server-header: nginx/1.18.0 (Ubuntu) |_http-title: 403 Forbidden Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel ... |
绕过防火墙/安全设备
Nmap使用默认User-Agent,流量和日志里一览无遗(秃子头上的虱子),不封你封谁。大部分工具默认指纹都已被提取规则,使用的时候注意看下源码或者测试一下。
![]()
扫描时指定User-Agent,可以绕过部分安全检测
nmap -A -v -p80 124.*.8.254 --script http-methods --script-args http.useragent="Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0" |
结果写入文件
原始结果
nmap -A -v -p80 -T4 124.*.8.254 -o 4.txt |
保存为XML格式
nmap -A -v -p80 -T4 124.*.8.254 -oX 4.xml |
参考:
-
PING/ICMP
-
SYN扫描/半开放扫描
Masscan用法
Masscan是一个互联网规模的端口扫描仪。它可以在5分钟内扫描整个互联网,从一台机器每秒传输1000万个数据包。这是我常用的端口扫描工具,老规矩先放我最常用参数组合,想了解原理继续看,不想了解直接套用。
masscan -p80,8000-9000 182.92.106.58 --rate=10000 --banners --source-port 61000 --http-user-agent "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0" -Pn |
编译安装
vulab@sechelper:~$ apt install make gcc git -y vulab@sechelper:~$ git clone https://github.com/robertdavidgraham/masscan.git vulab@sechelper:~$ cd masscan vulab@sechelper:~/masscan$ make && make install ... c -g -ggdb -Wall -O2 -c src/stub-pfring.c -o tmp/stub-pfring.o cc -g -ggdb -Wall -O2 -c src/syn-cookie.c -o tmp/syn-cookie.o ... cc -g -ggdb -Wall -O2 -o bin/masscan tmp/crypto-base64.o tmp/crypto-blackrock2.o tmp/event-timeout.o tmp/in-binary.o tmp/in-filter.o tmp/in-report.o tmp/logger.o tmp/main-conf.o tmp/main-dedup.o tmp/main- ... |
vulab@sechelper:~/masscan$ masscan -h # 出现帮助信息表示安装成功 usage: masscan -p80,8000-8100 10.0.0.0/8 --rate=10000scan some web ports on 10.x.x.x at 10kpps masscan --nmaplist those options that are compatible with nmap masscan -p80 10.0.0.0/8 --banners -oB <filename>save results of scan in binary format to <filename> masscan --open --banners --readscan <filename> -oX <savefile>read binary scan results in <filename> and save them as xml in <savefile> vulab@sechelper:~/masscan$ masscan --help MASSCAN is a fast port scanner. The primary input parameters are the IP addresses/ranges you want to scan, and the port numbers. An example is the following, which scans the 10.x.x.x network for web servers:masscan 10.0.0.0/8 -p80 The program auto-detects network interface/adapter settings. If this fails, you'll have to set these manually. The following is an example of all the parameters that are needed:--adapter-ip 192.168.10.123--adapter-mac 00-11-22-33-44-55--router-mac 66-55-44-33-22-11 Parameters can be set either via the command-line or config-file. The names are the same for both. Thus, the above adapter settings would appear as follows in a configuration file:adapter-ip = 192.168.10.123adapter-mac = 00-11-22-33-44-55router-mac = 66-55-44-33-22-11 All single-dash parameters have a spelled out double-dash equivalent, so '-p80' is the same as '--ports 80' (or 'ports = 80' in config file). To use the config file, type:masscan -c <filename> To generate a config-file from the current settings, use the --echo option. This stops the program from actually running, and just echoes the current configuration instead. This is a useful way to generate your first config file, or see a list of parameters you didn't know about. I suggest you try it now:masscan -p1234 --echo |
-p 指定端口
vulab@sechelper:~/masscan$ sudo masscan -p 80 124.*.8.1/24 Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-09-05 02:12:22 GMT Initiating SYN Stealth Scan Scanning 256 hosts [1 port/host] Discovered open port 80/tcp on 124.*.8.177 Discovered open port 80/tcp on 124.*.8.39 Discovered open port 80/tcp on 124.*.8.7 Discovered open port 80/tcp on 124.*.8.186 Discovered open port 80/tcp on 124.*.8.13 Discovered open port 80/tcp on 124.*.8.77 Discovered open port 80/tcp on 124.*.8.163 Discovered open port 80/tcp on 124.*.8.133 ... |
–rate=10000 发包频率,数值越大扫描越快,根据自己网络设置,频率太高误报越高
vulab@sechelper:~/masscan$ sudo masscan -p 80 124.*.8.1/24 --rate=10000 |
**–banners 指纹信息,配合 –source-port 61000 一起使用 **
Tcp协议连接目标端口时会在系统内分配一个端口与目标通讯,因为有时候从目标返回数据包会被防火墙过滤丢弃,导致masscan无法获取banner信息,所以需要设置一个固定的源端口,方便在防火墙配置白名单不丢弃/拦截此端口数据。
vulab@sechelper:~/masscan$ sudo iptables -A INPUT -p tcp --dport 61000 -j DROP |

vulab@sechelper:~/masscan$ sudo masscan -p 80 124.*.8.254 --banners --source-port 61000 --rate=10000 Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-09-05 03:06:20 GMT Initiating SYN Stealth Scan Scanning 1 hosts [1 port/host] Discovered open port 80/tcp on 124.*.8.254 Banner on port 80/tcp on 124.*.8.254: [http.server] nginx/1.18.0 (Ubuntu) Banner on port 80/tcp on 124.*.8.254: [title] 403 Forbidden Banner on port 80/tcp on 124.*.8.254: [http] HTTP/1.1 403 Forbidden\x0d\x0aServer: nginx/1.18.0 (Ubuntu)\x0d\x0aDate: Mon, 05 Sep 2022 03:06:22 GMT\x0d\x0aContent-Type: text/html\x0d\x0aContent-Length: 162\x0d\x0aConnection: close\x0d\x0a\x0d |
绕过安全检测
在源码masscan/src/proto-http.c中预定义的User-Agent各大厂商肯定已经提取指纹规则,还在使用默认User-Agent不封你封谁,大部分工具默认指纹都已被提取规则,使用的时候注意看下源码或者测试一下。

服务器日志里看的清清楚楚,溯源一抓一个准。

扫描时指定User-Agent,可以绕过部分安全检测
vulab@sechelper:~/masscan$ sudo masscan -p 80 124.*.8.254 --banners --source-port 61000 --rate=10000 --http-user-agent "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0" Starting masscan 1.3.2 (http://bit.ly/14GZzcT) at 2022-09-05 03:15:14 GMT Initiating SYN Stealth Scan Scanning 1 hosts [1 port/host] Discovered open port 80/tcp on 124.*.8.254 Banner on port 80/tcp on 124.*.8.254: [http.server] nginx/1.18.0 (Ubuntu) Banner on port 80/tcp on 124.*.8.254: [title] 403 Forbidden Banner on port 80/tcp on 124.*.8.254: [http] HTTP/1.1 403 Forbidden\x0d\x0aServer: nginx/1.18.0 (Ubuntu)\x0d\x0aDate: Mon, 05 Sep 2022 03:15:16 GMT\x0d\x0aContent-Type: text/html\x0d\x0aContent-Length: 162\x0d\x0aConnection: close\x0d\x0a\x0d |
-Pn 扫描前不PING,直接开扫
vulab@sechelper:~/masscan$ sudo masscan -p 80 124.*.8.254 --banners --source-port 61000 --rate=10000 --http-user-agent "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0" -Pn |
结果写入文件
-oJ 保存为Json格式
sudo masscan -p 80 124.*.8.254 --banners --source-port 61000 --rate=10000 --http-user-agent "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0" -oJ 22090501.json |
-oX 保存为XML格式
sudo masscan -p 80 124.*.8.254 --banners --source-port 61000 --rate=10000 --http-user-agent "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0" -oJ 22090501.xml |
重定向输出,保存为原始格式
sudo masscan -p 80 124.*.8.254 --banners --source-port 61000 --rate=10000 --http-user-agent "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:87.0) Gecko/20100101 Firefox/87.0" > 22090501.txt |
Zmap
ZMap是一种快速的单包网络扫描仪,专为互联网范围内的网络调查而设计。在具有千兆以太网连接的典型台式计算机上,ZMap能够在45分钟内扫描整个公共IPv4地址空间。
编译安装
sudo apt-get install build-essential cmake libgmp3-dev gengetopt libpcap-dev flex byacc libjson-c-dev pkg-config libunistring-dev git -y git clone https://github.com/zmap/zmap.git cmake . make -j4 |
老规矩先放我最常用参数组合,想了解原理继续看,不想了解直接套用。
sudo zmap -B 1M -p80 --source-port=61000 124.*.8.1/24 -o 22090501.txt |
参数解释
-B 扫描速率最大带宽
-p 端口号,单一
-o 输出到文件
zgrab
ZGrab是一种快速、模块化的应用层网络扫描仪,用于完成大型互联网范围的调查。ZGrab配合ZMap一起使用。
老规矩先放我最常用参数组合,想了解原理继续看,不想了解直接套用。
./zgrab2 http -p 80 -f 22090501.txt -o 22090502.json --user-agent="Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.95 Safari/537.36" |
zmap和zgrab2联合使用
sudo zmap -B 1M -p80 --source-port=61000 124.*.8.1/24|ztee 22090503.csv| ./zgrab2 http -p80 --user-agent="Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.95 Safari/537.36" -o 22090504.json |
编译安装
sudo apt install golang-go git clone https://github.com/zmap/zgrab2.git cd zgrab2 make |
使用刚才ZMap扫描结果,探测http服务的Banner信息
./zgrab2 http -f 22090501.txt -o 22090502.json |
http端口默认是80,可以自行指定非默认端口的http服务
./zgrab2 http -p 8080 -f 22090501.txt -o 22090502.json |
查看模块的帮助信息,例如查看http这个模块有哪些可设置参数
vulab@sechelper:~/zgrab2$ ./zgrab2 http -h Usage:zgrab2 [OPTIONS] http [http-OPTIONS] ... [http command options]-p, --port= Specify port to grab on (default: 80) ...--user-agent= Set a custom user agent (default: Mozilla/5.0 zgrab/0.x) ... |
绕过安全检测
查看服务器日志User-Agent一眼看出是zgrab在探测,默认的User-Agent是Mozilla/5.0 zgrab/0.x
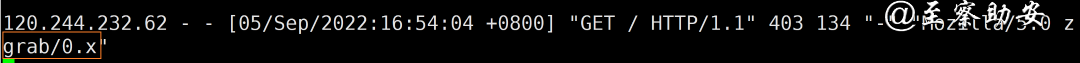
vulab@sechelper:~/zgrab2$ ./zgrab2 http -p80 --user-agent="Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_2) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.95 Safari/537.36" -f 22090501.txt 关注 至察助安 ,专注网络安全优质知识分享,无优质,不分享。
